How Health Care Providers Can Thwart Cyber Attacks (Part 2)
This is an excerpt from the paper “How Health Care Providers Can Thwart Cyber Attacks”, focused on the Key Messages and Failure Causes.
BCG — Boston Consulting Group
By Michael Coden and Mike Czumak
Edited by Joaquim Cardoso
APRIL 20, 2021
Key messages
- The number of cyber attacks on health care systems has reached epidemic proportions.
- Health care providers and hospitals should focus on six primary threats: (1) Hacking; (2)Phishing; (3) Malware; (4) Espionage; (5) Compromised Accounts; and (6) Unauthorized Data Disclosures
- Five Steps to Take Immediately:
- Determine and prioritize the most critical data and cyber-physical assets
- Assess the risks and determine the key actions for reducing them
- Educate and render risky employee cyber behaviors “irrelevant.”
- Develop crisis management and cybersecurity incident response teams.
- Conduct tabletop exercises (TTXs).
- To ensure their systems are protected by cyber threats over the long haul, hospitals need to consider six strategic imperatives:
- Design cybersecurity measures into systems from the start
- Ensure continued IT system hygiene and governance
- Map the cybersecurity strategy to the business strategy
- Scale systems safely and cost-effectively
- Assume an attack is inevitable
- Prepare for simultaneous disasters
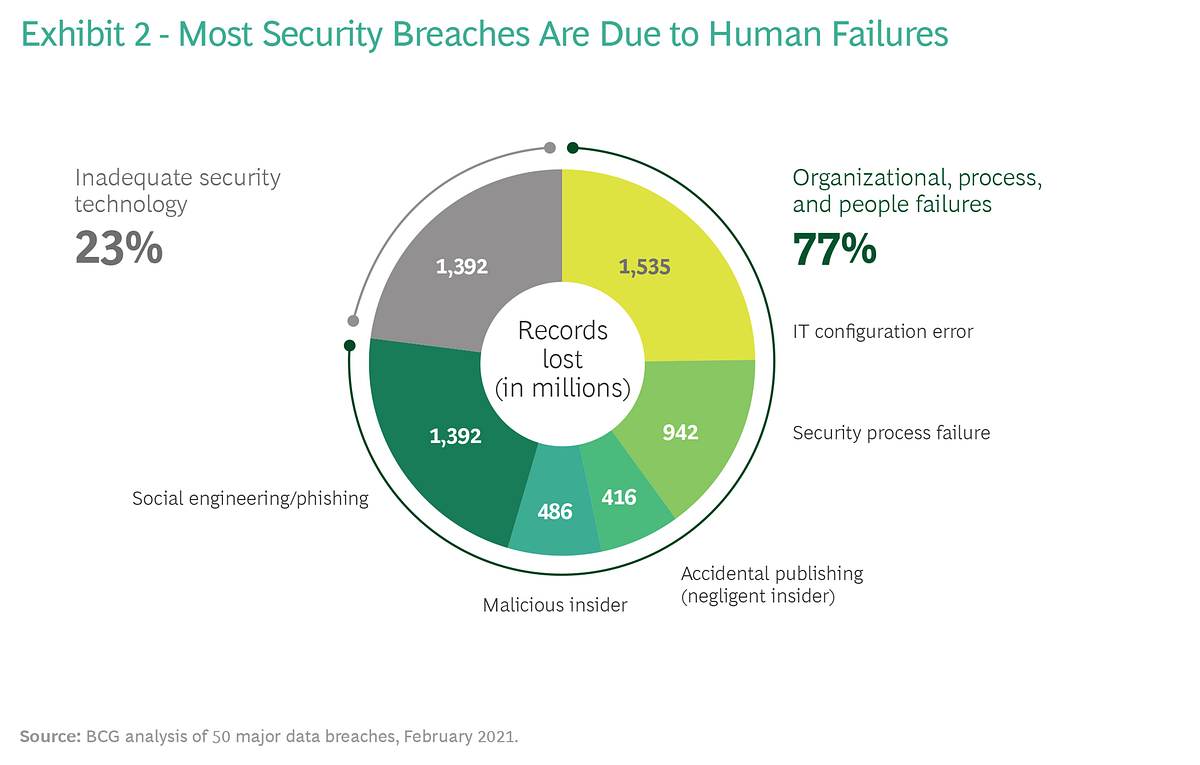
Excerpt: Main causes of Cyber Attacks
BCG analysis found that 77% of all cyber attacks are due to human failures and only 23% to tech glitches. (See Exhibit 2.)
Consequently, it’s paramount for hospitals to assess behaviors that put health care systems at risk and make those behaviors “irrelevant” so that employees default to more-secure behaviors.
But getting employees to adopt different behaviors is difficult.
Many users are simply looking for the quickest and easiest way to get their job done.
Rather than outright prohibiting things like collaboration or file sharing, hospitals should consider providing securely configured and managed enterprise solutions like Box, Office 365, G-Suite, or Slack, which can help reduce the use of personal accounts while putting the necessary oversight and risk reduction controls in place.
Additionally, technical safeguards like disabling unsigned macros and sandboxing (separating apps from critical resources) can mitigate the fallout from users opening attachments or clicking malicious links.
While technical controls are key to a robust risk mitigation strategy, they are not a replacement for a strong culture of security awareness.
It’s critical both to show employees why cybersecurity is as vital as safety and ethics and to teach them how to avoid causing an incident in the future.
In addition, hospitals should consider not only punishing risky behavior but also acknowledging and rewarding good security practices.
MSK has implemented a security awareness program that leverages activities such as formal training, webinars, office hours, contests, and organization-wide phishing assessments.
Developing the necessary playbook and response plan is also essential. Like MSK, many hospitals already have an incident command team that responds to significant events.
Instead of creating a completely new team, organizations may prefer to develop response plans that leverage the processes, participants, and command structure of the existing group.
Cyber events may require additional participants and workstreams, but using familiar, well-tested procedures can ensure a more seamless response.
About the authors
Michael Coden
Managing Director, BCG Platinion
New York
Mike Czumak
Chief Information Security Officer, Memorial Sloan Kettering Cancer Center
Originally published at https://www.bcg.com on April 14, 2021.
PDF version of the full versionhttps://joaquimcardoso.blog/media/c79d76537f0bd0ec6e02ac192a51c298